tsg
17. Juni 2024 um 07:03
1
Hallo,
vielleicht für den einen oder anderen interessant.
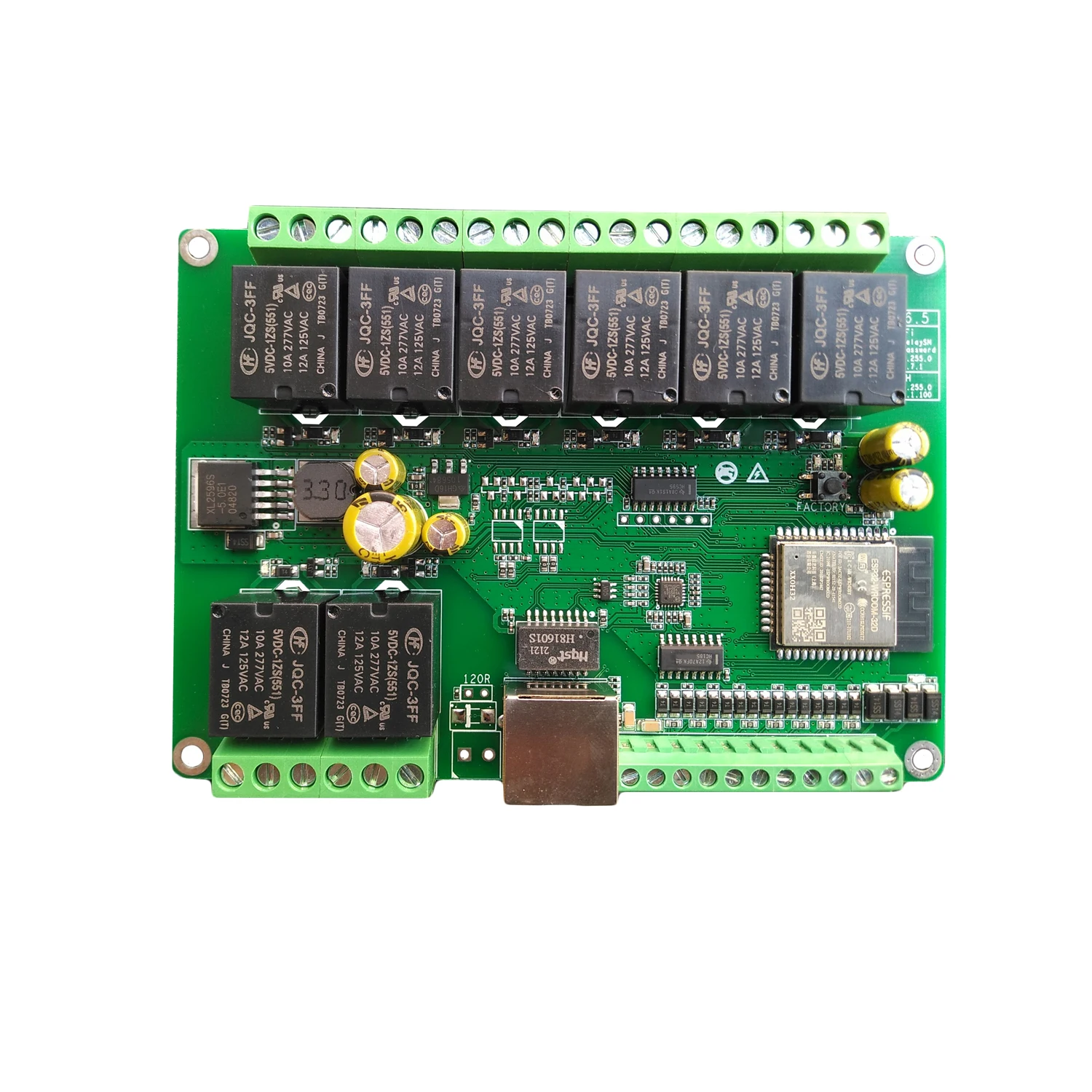
Ich habe hier ein sehr schönes Modul von http://www.dingtian-tech.com
Überteuert auch bei Amazon unter anderen Namen erhältlich.
Hier mal eine Übersicht:
Parameter
DT-R002
DT-R004
DT-R008
DT-R016
DT-R032
Foto
Schnitts telle
Ethernet, wifi, rs485 (optional), kann bus (optional), wiegand (optional)
Größe (Relais platine)
87*68mm
91.6*86,4mm
122*87mm
250*107mm
370*107mm
Größe (din35 Fall)
90*90*40mm
115*90*40mm
145*90*40mm
252*123*43mm
373*123*43mm
Strom versorgung
12v/24vdc, 5v/24vac
Netzteil
12VDC/0,5a
12VDC/0,5a
12VDC/0,5a
12vdc/2a
12vdc/3a
Strom verbrauch
2w
3w
5w
9w
16w
Arbeits temperatur
-20~75℃
Lagerte mperatur
-40~80℃
Protokoll
Mqtt/mqtts, modbus-rtu/tcp/ascii/udp, tcp, udp, http bekommen cgi, coap
Mengen relais
2do
4do
8do
16do
32do
Quantität digitaler Eingang
2di
4di
8di
16di
32di
Menge wiegand
1(optional)
1/2(optional)
0
1
1
Rtc
Keine
Keine
Keine
Optional
Optional
Hausa utomation
Domoticz, Heim assistent, openhab, roter Knoten
Funktion
Relais aufgabe (Zeitplan), Eingangs status, Eingangs verbindungs relais, Eingangs verbindungs url, Eingabe/Relais alias (Name),
Ip watchdog, transparente übertragung, ntp client, eingang gegenseitige steuerung, ota upgrade
Ethernet-IP
192.168.1.100
Web-Benutzer/pwd
Admin/Admin
Wifi ap ip
192.168.7.1
Wifi ap ssid/pwd
Dtrelaysn/dtpassword
Wifi sta ip
192.168.1.97
Unterlagen zu den Modulen:
Dingtian Relay Development Board Demo source code
ESPHome Config:
Domoticz Dingtian Relay Plugin:
Dingtian Relay Python Plugin for Domoticz
Tasmota:
Zu meinen Projekten:
Aktuell habe ich ein 4-CH Modul im Test (nur Relais / IO) + RS485, wobei über MQTT in HA Integration einfach ist. Mit dem RS485 komme ich noch nicht klar. Vermutlich werde ich jetzt ESPHome flashen und hier den ModBus-Controller verwenden.
Ein 2CH Modul ist bestellt und ist für die SG-Ready Schnittstelle der LWWP geplant.
Das 4CH Modul soll in Verbindung eines SDMxxx RS485 Energymeter dann eine PV-Heizstab Steuerung übernehmen.
Alternativ kann über ein Modul RX485 auf 4-20mA/0-10V auch ein z.B. ein Leistungssteller im xxkW Bereich eine stufenlose Regelung vorgenommen werden.
Zusammen mit dem Gehäuse, eine fertige Elektronik die mit 12V gespeist werden kann. ETH für Bereiche wo kein WIFI Verfügbar. Die Standard-SW schon ganz brauchbar und wer möchte kann sich das ganze umflashen. Echt eine geniale Kiste.
Bin gespannt auf eure Meinungen / Ideen.
tsg
18. Juni 2024 um 07:01
2
Ok Nachtrag: Vor dem Flash schauen ob secureboot / flashencrypthon akiv ist (scheint leider der Fall).
Hier eine Anleitung / Erläuterung:
offen 06:27PM - 30 Nov 21 UTC
geschlossen 11:00PM - 30 Nov 21 UTC
Hi,
i just bricked a voidmicro.com laserenvraver board by flashing fuidnc using… the windows batch script.
After uploading the esp stuck in a boot loop:
```
ets Jun 8 2016 00:22:57
rst:0x10 (RTCWDT_RTC_RESET),boot:0x37 (SPI_FAST_FLASH_BOOT)
flash read err, 1000
ets_main.c 371
```
The upload went flawlessly and i was able to verify the flash contents by using esptool.exe.
The issue is caused by secureboot and flashencryption set by the manufacturer.
These options do **not prevent the user from flashing** the device.
Flashing unencrypted binarys will render the device useless.
These security options cannot be disabled once activated.
Please refer to:
https://docs.espressif.com/projects/esp-idf/en/latest/esp32/security/secure-boot-v1.html
https://docs.espressif.com/projects/esp-idf/en/latest/esp32/security/flash-encryption.html
https://limitedresults.com/2019/11/pwn-the-esp32-forever-flash-encryption-and-sec-boot-keys-extraction/
After flashing the esp32 the original flash-contents are no longer present. Using the described attack vector to obtain the AES Keys is no longer possible (and far to complicated).
I end up replacing the esp32 on that board.
The flash-scripts should be extended to use expfuse.exe prior to flashing the device.
If security options are set, inform the User:
_This chip is not able to run any other firmware than the original due to security options set by the manufacturer!
Using other flash methods may seem to work, but will brick the device!
Don't do it, SERIOUSLY!_
Here is a espfuse-summary of my bricked esp32:
```
C:\Users\m-sja\Downloads\fluidnc-v3.2.5\win64>espefuse.exe -p com7 -b 115200 -c esp32 summary
Connecting...
Device PID identification is only supported on COM and /dev/ serial ports.
...........
espefuse.py v3.2
EFUSE_NAME (Block) Description = [Meaningful Value] [Readable/Writeable] (Hex Value)
----------------------------------------------------------------------------------------
Calibration fuses:
BLK3_PART_RESERVE (BLOCK0): BLOCK3 partially served for ADC calibration data = False R/W (0b0)
ADC_VREF (BLOCK0): Voltage reference calibration = 1100 R/W (0b10000)
Config fuses:
XPD_SDIO_FORCE (BLOCK0): Ignore MTDI pin (GPIO12) for VDD_SDIO on reset = False R/W (0b0)
XPD_SDIO_REG (BLOCK0): If XPD_SDIO_FORCE, enable VDD_SDIO reg on reset = False R/W (0b0)
XPD_SDIO_TIEH (BLOCK0): If XPD_SDIO_FORCE & XPD_SDIO_REG = 1.8V R/W (0b0)
CLK8M_FREQ (BLOCK0): 8MHz clock freq override = 50 R/W (0x32)
SPI_PAD_CONFIG_CLK (BLOCK0): Override SD_CLK pad (GPIO6/SPICLK) = 0 R/W (0b00000)
SPI_PAD_CONFIG_Q (BLOCK0): Override SD_DATA_0 pad (GPIO7/SPIQ) = 0 R/W (0b00000)
SPI_PAD_CONFIG_D (BLOCK0): Override SD_DATA_1 pad (GPIO8/SPID) = 0 R/W (0b00000)
SPI_PAD_CONFIG_HD (BLOCK0): Override SD_DATA_2 pad (GPIO9/SPIHD) = 0 R/W (0b00000)
SPI_PAD_CONFIG_CS0 (BLOCK0): Override SD_CMD pad (GPIO11/SPICS0) = 0 R/W (0b00000)
DISABLE_SDIO_HOST (BLOCK0): Disable SDIO host = False R/W (0b0)
Efuse fuses:
WR_DIS (BLOCK0): Efuse write disable mask = 388 R/W (0x0184)
RD_DIS (BLOCK0): Efuse read disable mask = 3 R/W (0x3)
CODING_SCHEME (BLOCK0): Efuse variable block length scheme
= NONE (BLK1-3 len=256 bits) R/W (0b00)
KEY_STATUS (BLOCK0): Usage of efuse block 3 (reserved) = False R/W (0b0)
Identity fuses:
MAC (BLOCK0): Factory MAC Address
= 40:f5:20:81:b4:04 (CRC 0xe0 OK) R/W
MAC_CRC (BLOCK0): CRC8 for factory MAC address = 224 R/W (0xe0)
CHIP_VER_REV1 (BLOCK0): Silicon Revision 1 = True R/W (0b1)
CHIP_VER_REV2 (BLOCK0): Silicon Revision 2 = False R/W (0b0)
CHIP_VERSION (BLOCK0): Reserved for future chip versions = 2 R/W (0b10)
CHIP_PACKAGE (BLOCK0): Chip package identifier = 1 R/W (0b001)
MAC_VERSION (BLOCK3): Version of the MAC field = 0 R/W (0x00)
Security fuses:
FLASH_CRYPT_CNT (BLOCK0): Flash encryption mode counter = 1 R/- (0b0000001)
UART_DOWNLOAD_DIS (BLOCK0): Disable UART download mode (ESP32 rev3 only) = False R/- (0b0)
FLASH_CRYPT_CONFIG (BLOCK0): Flash encryption config (key tweak bits) = 15 R/W (0xf)
CONSOLE_DEBUG_DISABLE (BLOCK0): Disable ROM BASIC interpreter fallback = True R/W (0b1)
ABS_DONE_0 (BLOCK0): Secure boot V1 is enabled for bootloader image = True R/W (0b1)
ABS_DONE_1 (BLOCK0): Secure boot V2 is enabled for bootloader image = False R/W (0b0)
JTAG_DISABLE (BLOCK0): Disable JTAG = True R/W (0b1)
DISABLE_DL_ENCRYPT (BLOCK0): Disable flash encryption in UART bootloader = True R/W (0b1)
DISABLE_DL_DECRYPT (BLOCK0): Disable flash decryption in UART bootloader = True R/W (0b1)
DISABLE_DL_CACHE (BLOCK0): Disable flash cache in UART bootloader = True R/W (0b1)
BLOCK1 (BLOCK1): Flash encryption key
= ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? -/-
BLOCK2 (BLOCK2): Secure boot key
= ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? -/-
BLOCK3 (BLOCK3): Variable Block 3
= 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 R/W
Flash voltage (VDD_SDIO) determined by GPIO12 on reset (High for 1.8V, Low/NC for 3.3V).
```
and a espfuses-dump of my bricked esp32:
```
C:\Users\m-sja\Downloads\fluidnc-v3.2.5\win64>espefuse.exe -p com7 -b 115200 -c esp32 dump fuse.hex
Connecting...
Device PID identification is only supported on COM and /dev/ serial ports.
BLOCK0 ( ) [0 ] read_regs: 00130184 2081b404 00e040f5 0000a200 00001032 f0000000 000003d4
BLOCK1 (flash_encryption) [1 ] read_regs: 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000
BLOCK2 (secure_boot_v1 s) [2 ] read_regs: 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000
BLOCK3 ( ) [3 ] read_regs: 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000
EFUSE_REG_DEC_STATUS 0x00000000
```
Here is a espfuse-dump of the new esp32:
```
C:\Users\m-sja\Downloads\fluidnc-v3.2.5\win64>espefuse.exe -p COM7 -b 115200 dump
Connecting.....
Detecting chip type... Unsupported detection protocol, switching and trying again...
Connecting...
Detecting chip type... ESP32
BLOCK0 ( ) [0 ] read_regs: 00000000 a49b4224 007a30ae 00008200 00000036 00000000 00000004
BLOCK1 (flash_encryption) [1 ] read_regs: 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000
BLOCK2 (secure_boot_v1 s) [2 ] read_regs: 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000
BLOCK3 ( ) [3 ] read_regs: 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000
EFUSE_REG_DEC_STATUS 0x00000000
```
The first section of Block0 is the interesting one.
As one of your projects goals is lo lower the barrier to for new users, it should be obvious also protect them from bricking their devices wherever possible.
Thank you very much for all the effort you put in these cnc-projects!!!
If you have any questions, i'll try to help as best as i can.
Best regards
Marian
Es gibt wohl eine Möglichkeit diese auch ohne "Sicherung" zu beziehen:
"When ordering this board ask for relay board with test firmware, otherwise the ESP32 will be locked."